Why Security is becoming important and crucial in current IT trend day by day? Security is an area that should be brought up to the close attention to people almost from all walks of life and not only should be restricted to the IT and business world, but also to the government agencies, activists, political team, NGO, stay at home people etc.
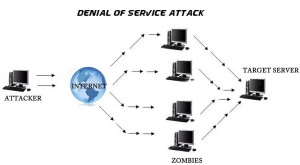
Let me begin with some of the recent security attack incidents and subsequent impact that we heard about. A Polish airliner LOT had to cancel flights and appx. 1500 passengers were stranded in warsaw airport. Airliner’s system was stalled and couldn’t send the required documents to the aircraft before takeoff. Documents would have flight route, weather details etc. and without that aircraft would not take off. All of a sudden, LOT system stalled because it faced DDoS (Distributed denial of service) attack. DDoS is a type of cyber attack in which loads of fake request are sent to the web server choking its capacity to serve requests while stalling system due to huge resource stress due to unsolicited consumption by such requests.
We were informed about security breach in one of the password manager “LastPass”. This application is programmed to store and manage hundreds of passwords and other credentials for users for different accounts, website etc. Company blog site reported that neither encrypted user vault data was taken, nor user accounts were accessed, however account email address, password reminders, server per user salts, and authentication hashes were compromised. This application could have been an inevitable attacking area for bad guys, what else could be better for hackers than this to hack system and get millions of personal information and passwords. This immediate issue required users to change their master password (1st level password to encrypt user vault) while company resorted to strengthen the security by involving ethical hacker, big bounty program, enabling 2 factor authentication and few more.
There has been a massive data breach reported by US Personnel Management agency. In the 1st week of June, Personnel management system for US government was hacked and data was compromised. The data contained personal and security information for people and used to screen and gives security clearance for federal job. Hackers found out the hole in the system and compromised data. Where was that hole, and how was that left undetected? Whether it was at firewall or access level, port , application, web server or something else?
In the past we had seen instances of data breach in SONY, Target, Home Depot and few other retailers. Bad guys know that amount of golden data about customers’ details; credit card information etc. would be huge that can give them tons of avenue to mint wealth.
“Target” reported to have lost 40 million card numbers during holiday shopping. Similar incident was reported by “Neiman Marcus”. “White lodging”, a hotel franchise management company also reported similar incident in February 2014. On further we heard about, “Sally Beauty” , “Michaels” (US arts and crafts chain), “Affinity Gaming” (That operates 11 casinos in the US), “PF Changs” (Restaurant operator), “Albertsons & SuperValu”, “Community Health Systems” (Patients Data), “UPS” (US leading parcel service), “Dairy Queen” and many more, leading to confidential data breach containing Credit, Debit card number, name and SSN as well. The root cause post investigation reported to had “Malicious software” that was installed into the system that would collect payment card data from customers who purchased during certain interval.
We have also seen the “CryptoLocker” virus attack as ransomware Trojan that would encrypt file and ask money to decrypt the same. This impact is even bitter if data copy is not in place and you don’t have any other means to restore/recover data than paying the ransom to get required code.

As IT landscape is changing and evolving fast, getting better and smarter with new ideas, tools and concepts, so are the bad guys. So security is an area that would continue going back and forth in calibrating approach while learning from defects, but in the nutshell it is getting smarter and better. Besides, we have heard about security hole in OpenSSL protocol resulted into “HeartBleed”,
Reported security Flaws such as GHOST(in Jan/15), JASBERG(in Feb/15),FREAK(in Mar/15),VENOM(in May/15),LogJam(in May/15) etc. and many more and I can’t cover all those in this blog, have been giving us strong feeling about our vulnerability relative to IT set up . Every year we get to see some or the other security threat.
Type of security breach and measures to protect system: There are tons of ways to affect your systems. Malware is something that can be downloaded and its executable program can run without user’s knowledge. I have seen people are generally logged into their home computer using admin privileges. While they or someone else (may be kids) browse internet and download games or some not so authenticated information, chances are high that malicious program could be downloaded in their system and run the code without users intention. I advise not to keep users privileges as admin but a general users (Windows system), keep admin privilege only with you and use that when you are sure what you are downloading and/or running.
I have seen people making banking transactions, email etc. near café, hotel etc. using hotspots or free Wifi. An IT personal with some network skill can easily get to wifi data through his device and get your user id and password. We need to ensure that site has got lock/green block with HTTPS protocol (Http +SSL) that ensures encryption and data security is in place.
Web application has become life line for almost everything from personal requirement to professional transaction requiring port 80 to stay always open to serve the purpose. Once a bad guy/hacker gets access to the web application can retrieve information from DB, get files from root directory, and send malicious codes to the web server etc. while damaging privacy and stealing information either at home or office. Measures to protect such damages starts from application development through test to infrastructure set up.
Application developer needs to design and develop code keeping security test in mind such as buffer overflow, cross site scripting etc. Coder should take adequate learning from the best practices and institutes such as SANS, utilize OWASP top ten as a guidance to secure coding, etc. Web Inspect tool should be used to screen potential security flaw in advance. I strongly recommend developers refer to OWASP guide @ https://www.owasp.org. Design flow should give special focus to “User Authentication” module while evaluating basic access authentication to integrated (SSO) authentication requirement. This follows authorization module that deals with designing ability for adequate access ranging from basic to special privileges types. While dealing with session management, developers should think how to trap scenario of web attack such as replay, man in the middle attack, request forging etc. Authorization enforcement and request avoidance should be designed at application/session management level while session is being maintained with proper encryption.
Designer/coder should also make adequate provision for proper log file to capture relevant transaction that helps in diagnosis and putting in proper rectification. SQA is one of the most crucial phases that ensures data integrity and confidentiality while application writes erases or communicate the same. In the maintenance phase, effort should be there to continue decreasing the attack surface area in the production life cycle.
Infrastructure region must be adequately configured to ensure data security including confidentiality, integrity and accessibility. This concerns physical security at DC, segregation of data (System, business, clients, employees related) with proper SOD (Separation of Duty) matrix. Firewall could be one of the solutions to achieve control and maintain logical isolation amongst different variety of data. Infrastructure stack should be equipped with system level access control that helps maintain isolation and avoid any type of security breach. Network layer should be designed to ensure encryption for all authenticated and authorized transaction. Two factor authorization should be enforced in the process e.g. combination of SSH key and time dependent could go as key.
OS and applications need to be thoroughly updated with security patches. Recently we encountered a security issue with Flash player application (Adobe) known as Zero-Day for flash player. The bug was left undiscovered by the developers/vendor that was later exploited by bunch of hackers. Flash releases patch to fix that. We must always keep applications those are vulnerable such as browser chrome, IE, Flash, vendor applications etc. for both security and features.
IT evolution and security
Success of IOT drive depends upon how effectively and seamlessly security can be implemented in participating devices. M2M protocol talks to the machine on the fly without sending data & signal up to the server; this can be adopted once we institute a robust security mechanism/policy and protocol in IOT ecosystem.
Ongoing Cloud development, BYOD etc. drive requires security as a first project to be tested & implemented. We are optimizing infrastructure resources for better TCO and faster performance while putting security a cumbersome solution. User profile, business data, system records etc. need to be controlled at multiple levels starting from a user, government, policy & compliance and business point of view.
In this BYOD world, let’s take a simple scenario of using smart phone to access personal mail as well as official documents including emails. If I use office WLAN to stay connected, use POP3 protocol to access personal email, then chances are high that any sneaky IT technicians (May be from N/W Team) can read my personal email. My strong recommendation here is to switch to HTTPS from POP3, that’s far more secure.
As we automate our personal and professional process, we depend ourselves to machine and underlying codes. We don’t have a perfect solution to replace human brain and emotional reflection that can arise in several situations warranting us a knee jerk reaction. We got to balance things here between machine and human. Let’s take a recent example of Keyless car that comes with pros and cons with mixed bag of security threat and solution but is still evolving, we can’t say it is 100% secured. This device has got a transmitter that transmit radio frequency to the car to operate engine and unlock steering automatically once car evaluates the signal, strength and other particulars. What if a bad guy gets an amplifier and relay signal from the keyless transmitter to the car? Bad guy would enter car and drive away. Potential solution could be to put the keyless device in a case that we call “Faraday Cage” that would not let radio signal to talk to the amplifier. But still bad guys would probably not give up and continue finding out ways to strike.
Security is a vast subject. It concerns data security, privacy, confidentiality, Integrity, Government regulation etc. Good amount of security exposures happened in the past resulting into changes in the policy (onset of PCI-DSS, HIPPA,SOX etc.) and product features (chip-n-pin in credit card, double authentication etc.) that should minimize instances for similar exposures.
In the summary, my attempt through this blog is to bring awareness about security in IT and professional ecosystem in the midst of fast changing IT landscape, design solution keeping security into huge consideration, evaluate and test product by hiring or becoming ethical hacker and last but not the least collaborate and learn from the mistakes by self or others while rectifying the solution.